WordPress Hacked: Effective Steps to Restore and Protect Your Website
All websites are susceptible to online threats, including hacking. If mishandled, this cybercrime can pose serious ramifications. For example, a hacked eCommerce site that collects personal information can jeopardize visitors’ data.
In WordPress, hacked websites have several indicators. Understanding them lets you quickly alleviate the threats and recover your site before causing further damage.
In this WordPress tutorial, we will explain how to identify if your site has been hacked and effective solutions to fix it. We will also explain preventive measures to help prevent a similar attack.
Download WordPress security checklist
Signs of a Hacked WordPress Website
In this section, you will learn six common indications of a hacked WordPress site.
Unable to Log In to the WordPress Dashboard
If you can’t log in to the WordPress dashboard despite entering the correct credentials, your website might be hacked.
This can happen if the attacker takes over admin accounts and changes the login credentials. Therefore, the WordPress site owners can’t access the dashboard to revoke the unauthorized access.
Unknown Redirection
Another sign of a hacked site is if it redirects to an unknown page. Usually, the perpetrators do this to send visitors to a phishing or malware-infested site for further attack.
Redirection can also be used to drive traffic to spam websites for financial gain or disrupt your page’s search engine optimization (SEO) ranking. It is also a common method for internet vandalism and defacement.
Changes in Website Content
Modified website content is a strong indication of a hacked WordPress website. For example, the attackers might put a link to redirect visitors to dangerous pages.
Unlike unknown redirection, this method is usually less noticeable. However, some cyber criminals intentionally change the entire page’s content to vandalize or send a message.
Sudden Traffic Drop
Your WordPress site might lose traffic when hacked due to unknown redirection. Content modifications can also cause this issue since they harm SEO.
Moreover, Google will exclude your website from the search results if the hackers infect it with malware or use it to engage in malicious activities, resulting in an organic traffic drop.
Unknown User Accounts with Admin Privilege
In addition to exploiting existing users, hackers who gain access to your WordPress site might create a new account with admin privileges. This account will let them manipulate your page from the inside.
To determine whether a potentially malicious user exists on your WordPress site, regularly check all accounts and their permissions via the admin dashboard.
Warnings on Browsers and SERPs
If your website is hacked, Google will show the “This site may be hacked” warning on the search engine result page (SERP).
Moreover, Google Chrome will display the “Deceptive site ahead” screen if your website security is compromised. If you encounter this message, verify your site’s status using the Google Safe Browsing tool.
11 Solutions to Fix a Hacked WordPress Website
After confirming that your WordPress is hacked, follow these 11 solutions to fix the website even if you can’t access the admin dashboard.
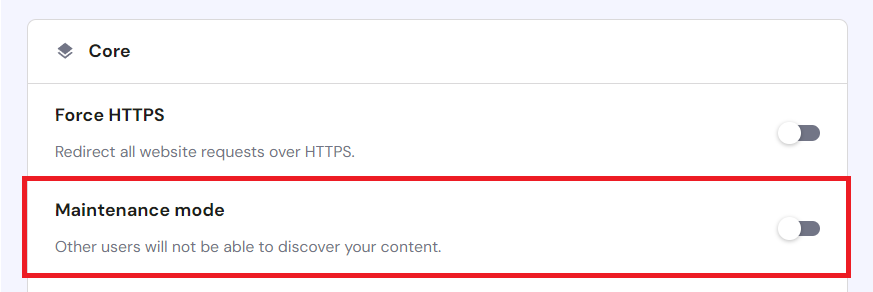
1. Put WordPress in Maintenance Mode
If you can access your admin dashboard, enable maintenance mode immediately. It will prevent visitors from opening your hacked WordPress site, protecting them from further damage.
Otherwise, you can do so by modifying the functions.php or .htaccess file. Check out our article on enabling WordPress maintenance mode to learn more about the steps.
Alternatively, Hostinger users can enable maintenance mode via their web hosting control panel, hPanel. After logging in to hPanel, navigate WordPress → Overview and turn on the Maintenance mode option.
2. Reset WordPress Password
If hackers can access your website, your login credentials are compromised. To avoid entailing threats, reset your WordPress admin, database, and hosting account passwords.
If you can get past the login page, do this via the WordPress admin panel. Otherwise, use the Lost Your Password form to recover your account. To access this, add /wp-login.php?action=lostpassword after your domain name in the browser. For example, www.domainname.com/wp-login.php?action=lostpassword.
Fortunately, Hostinger users can still access the admin dashboard to change their WordPress accounts’ passwords without logging in. To do so, go to hPanel → Websites → Admin Panel.
In addition to the WordPress admin password, we recommend updating all users’ credentials. It helps prevent follow-up attacks since the hacker might also gain access to multiple accounts.
3. Update WordPress
Before resolving your hacked website, update your old WordPress installations. It helps keep your website secure after the initial attack and prevents hackers from exploiting the content management system’s (CMS) vulnerabilities to undo your fix.
We have written an in-depth article on updating WordPress. In addition, we recommend patching your themes and plugins since some hackers also exploit them to infiltrate a website.
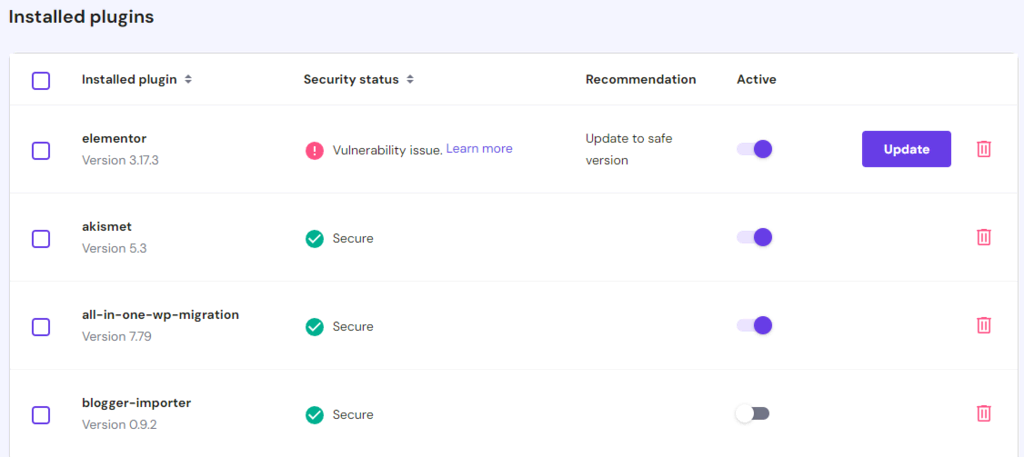
4. Deactivate Plugins and Themes
Since themes and plugins might have vulnerabilities, removing them helps minimize the attack surface and secure your WordPress site.
First, disable all plugins and themes. Then, reactivate them one by one to pinpoint the compromised ones. After identifying the faulty plugins and themes, delete them permanently to ensure your website is clean from malware.
To disable plugins, navigate to the wp-admin dashboard → Plugin → Installed Plugins. Click the Deactivate option under their name.
To do so in bulk, check the box next to them and select Deactivate from the drop-down menu. To remove them, select Delete on the deactivated plugins.
For themes, go to Appearance → Themes. Hover over their names and click Theme Details → Delete. Since you can’t deactivate them all simultaneously, you must check them individually.
You can also delete a WordPress theme from the hPanel by navigating to WordPress → Security panel. Moreover, our vulnerability scanner will notify you if there’s an unsafe plugin that you can deactivate or update.
5. Reinstall WordPress
If the hacker modifies or infects your WordPress core files with malware, you can only restore your website and reset all settings by reinstalling the CMS.
There are different ways to reinstall WordPress. If you can access the admin dashboard, navigate to the sidebar → Updates → Reinstall. Before doing this, ensure you have backed up your website content.
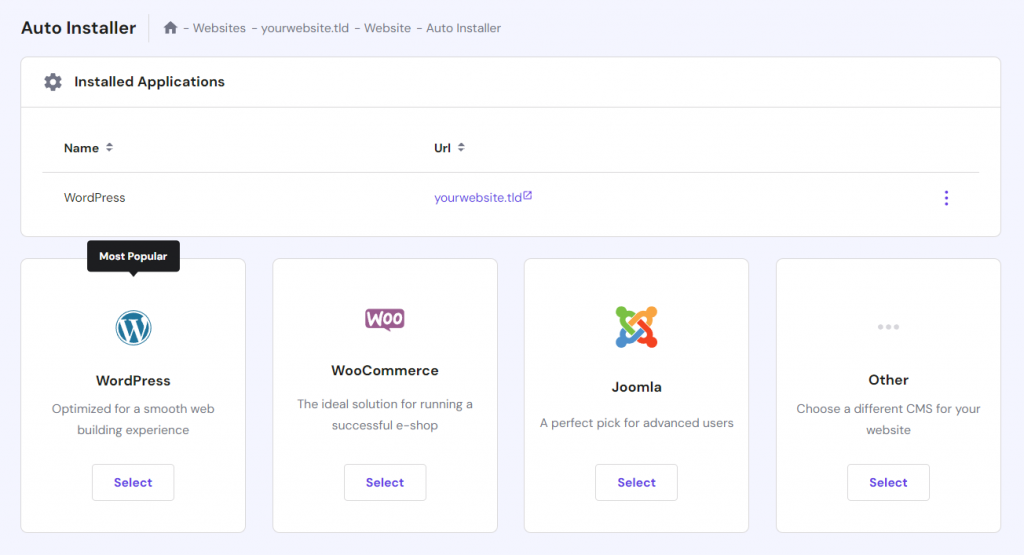
Otherwise, Hostinger users can install WordPress via hPanel by navigating to Auto Installer in their website management menu.
Alternatively, advanced users might prefer using the WP-CLI feature to reconfigure the CMS using commands.
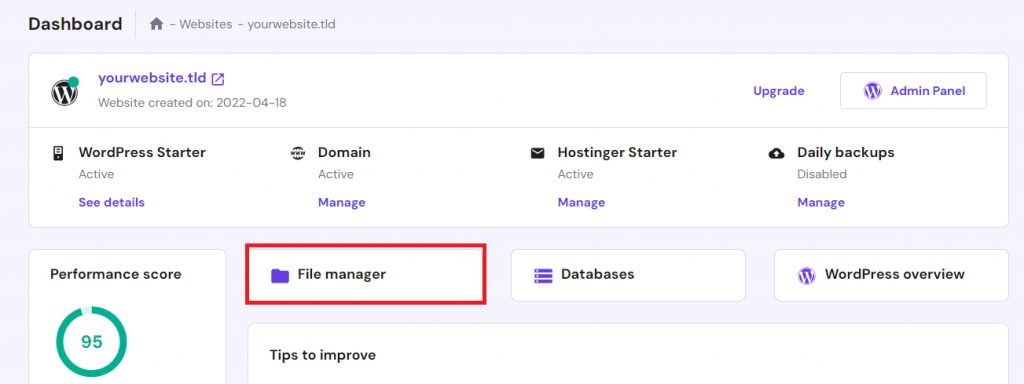
After reinstalling and clearing the threats, Hostinger users can reupload their website data using hPanel’s File Manager. Alternatively, use a file transfer protocol (FTP) client like FileZilla.
Optionally, remove unused WordPress installations as they might present vulnerabilities. To do so, delete the old data within the public_html folder.
Warning! If you are unsure about which WordPress system files to delete, don’t proceed since removing the wrong ones can break your website.
6. Remove New WordPress Users With Admin Privileges
Hackers might create a new WordPress admin account on your website to modify its settings from the inside. Removing or changing unknown user permissions helps alleviate the threats.
To check all website users and their privileges, open the admin dashboard → Users → All Users. Hover over accounts with the Administrator privilege and click Delete to remove them.
Alternatively, click Edit to manage the WordPress user’s role. Under the Role section, select another option to revoke the administrative privilege.
If you found multiple suspicious user accounts, remove them in bulk by checking the boxes next to their name and choosing Delete from the Bulk actions drop-down menu. You can also revoke their privileges simultaneously by selecting a new role in the Change role to… menu.
Remember to check in with other website administrators before deleting a user account since it’s irreversible.
7. Search for Malware
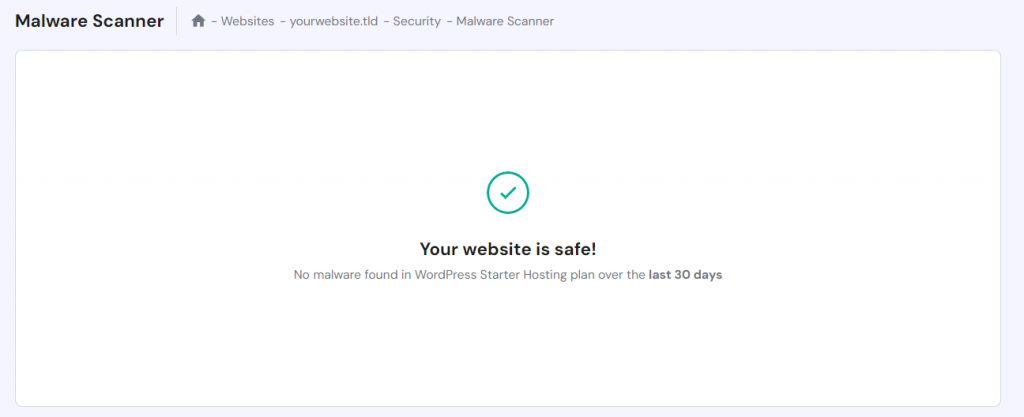
Hostinger’s Malware Scanner automatically scans for malware and removes threats. It also provides a security summary to simplify regular website check-ups.
Alternatively, you can use a plugin to remove malware from hacked WordPress sites. Check out our picks for the top 10 WordPress malware scanner plugins.
For example, Jetpack Protect users can remove malware by going to the admin dashboard sidebar → Jetpack → Protect → Scan. If the plugin found threats, click the Remove threat button.
For technical users who want to manually clean malware on their WordPress site, check our tutorial to learn more about the steps. However, be careful when using this method because an accidental misconfiguration might break your website.
8. Disable PHP Execution
Hackers can create backdoors in WordPress sites by injecting harmful files into the Uploads folder. You can prevent these malicious WordPress files from running by disabling PHP execution. Here are the steps:
- Open hPanel → Website and click Manage on the one you want to configure.
- Click File Manager to access the website content.
- Navigate to the wp-content/uploads/ folder.
- Click the Create New File icon on the sidebar.
- Name your file .htaccess and enter the following code:
<Files *.php> deny from all </Files>
- Press the disk icon on the top right to save the file.
However, other web hosting companies might not offer a file explorer feature. In this case, create a new .htaccess file on your computer and upload it to the root WordPress directory via the FileZilla FTP client.
We also recommend checking whether you set incorrect file permissions. Simply right-click the item and choose Permissions. The ideal value should be 644 for files and 744 for folders.
9. Clean the WordPress Database
Hackers might gain access to your WordPress site via SQL injection. To remove the threats, delete suspicious and unnecessary database records.
You can clean and optimize your WordPress database manually, but the process can be time-consuming. In addition, it’s also risky since deleting the wrong record can damage your website functionality.
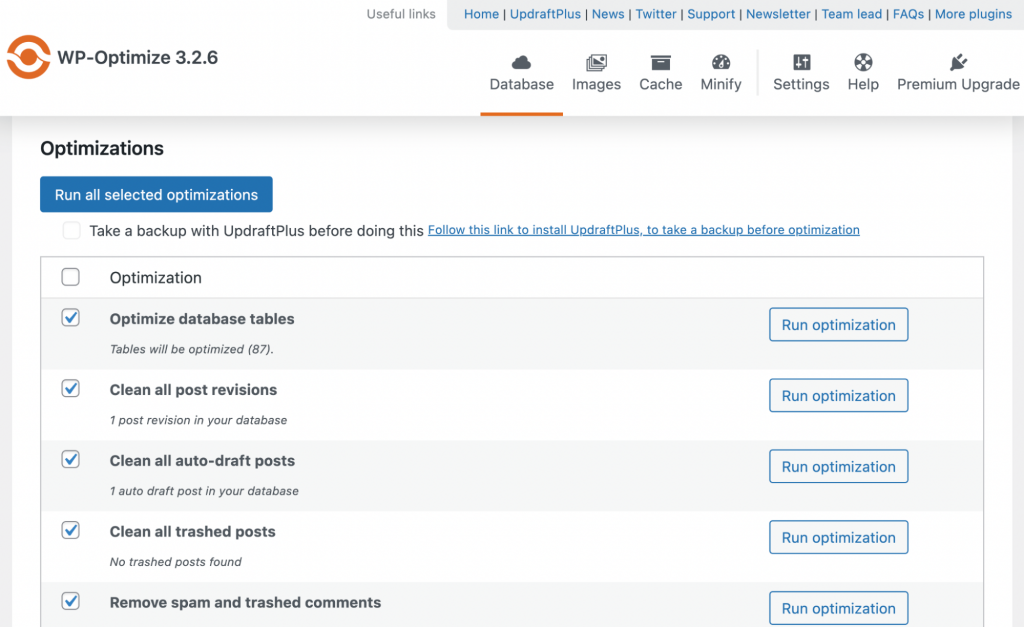
To automatically and safely clean your database, use WordPress plugins like WP-Optimize. After installing and activating it, follow these steps:
- Navigate to your WordPress dashboard sidebar → WP-Optimize → Database.
- Select or deselect the optimization options by clicking the boxes.
- Click Run all selected optimizations to start the cleaning process.
Before proceeding, create a backup of your website in case the WordPress database plugin accidentally deletes the wrong record.
10. Clean the WordPress Sitemap
A sitemap is a file containing data about your website content and page structure. It helps search engines find, crawl, and index your site in the results pages.
Hackers might attack your sitemap to find vulnerable entry points on your website. If a sitemap is compromised, search engines can’t index your site, which can result in traffic loss.
If your site has been hacked or infected with malware, create a new WordPress sitemap to recover its ranking. The easiest way to do this is by using an SEO plugin like Yoast.
Then, submit the new sitemap to Google Search Console so that Google will recrawl your website. It may take up to two weeks for your website to reappear on the SERP.
11. Contact Your Hosting Provider
If your website is hosted on a shared environment, it’s possible the cyber threat originated from another user within the same server. Contact your web host to check whether the security breach affects others or just you.
In addition, ask your web host to help clean the threats for you. At the minimum, it should be able to recover your access to the WordPress admin dashboard and provide logs showing IP addresses that accessed your server.
Your hosting provider must be able to ensure optimal website security. If your current web host can’t help mitigate WordPress hacking, consider finding a new host.
Pro Tip
Having difficulty resolving issues on your WordPress sites? Use Hostinger’s AI Troubleshooter to quickly find a solution.
We recommend a web host that offers 24/7 customer support to ensure you get immediate assistance if your WordPress site is hacked. With Hostinger, you will gain access to a Customer Success team that speaks multiple languages and is available around the clock via live chat.
Our WordPress hosting plan is also managed, meaning we will handle your server’s administration, such as security, updates, and backups. We also include various useful built-in tools, including the malware scanner.
How a WordPress Site Gets Hacked
Cybercriminals use various entry points and methods to hack a website. Here are some of the most common ways they exploit WordPress security issues:
- Backdoors ‒ injecting your WordPress installation with malware or exploiting unpatched vulnerabilities as an entry point. This attack can disturb operations and compromise personal data.
- Brute-force attacks ‒ gaining unauthorized access by guessing your website users’ login credentials, typically using bots. It might lead to performance issues or downtime if your website can’t handle the requests.
- Cross-Site Scripting (XSS) ‒ adding malicious scripts into a website’s code to execute an attack. It is used for stealing cookies, allowing hackers to impersonate the user and gather sensitive data.
- SQL injection attacks ‒ inserting malicious code into vulnerable SQL database requests. It can lead to data loss, identity spoofing, and information manipulation.
- Malicious redirects ‒ automatically moving your website visitors to a malicious web page. Hackers typically infect the destination with malware or put in a phishing form to get users’ personal information.
- Pharma hacks ‒ infecting your website with malicious content, typically pharmaceutical product ads. In addition to damaging SEO due to spammy keywords, it harms your brand reputation.
- Denial of Service (DoS) ‒ spamming your WordPress website with a large amount of traffic in a short period. It aims to shut down a website or a network by overwhelming it with requests.
How to Prevent Your Website from Being Hacked
To improve your site’s security and prevent WordPress hacking by cyber criminals, follow these best practices.
Use Secured Credentials
Common login credentials are risky because they are easy to guess. Instead of keeping a default username like “admin”, try to come up with a unique phrase.
For the password, include symbols, numbers, and uppercase letters to make it significantly harder to guess. We also recommend using at least eight characters since shorter combinations are quicker to decipher.
We recommend using a password manager like Bitwarden to store your credentials. Otherwise, create a passphrase so that it’s easier to remember. If you have it written, make sure to keep it in a secure location.
Important! Don’t use the same password for multiple accounts and change each of them regularly, at least every three months.
Use a Security Plugin
Use security plugins to help safeguard your website from hackers. For example, WordFence lets you enable two-factor authentication on your WordPress website, adding an extra layer of protection when their credentials are compromised.
Other popular security plugins are Advanced WordPress reCAPTCHA and WPS Limit Login. They are useful for verifying and limiting login attempts and preventing brute-force attacks.
If your web host doesn’t already provide a malware scanner, use a plugin like Jetpack Protect. In addition, set up a WordPress backup plugin to create a restore point and prevent data loss.
Remember to check each plugin’s reputation and reviews before installing it. A poorly maintained plugin can expose your website to threats instead of offering protection. Check out our picks for the best WordPress security plugins to learn more.
Always Check for Updates
Outdated WordPress files, themes, and plugins have known vulnerabilities that hackers will exploit to attack a website. Keeping them up-to-date ensures you have the latest security patches to minimize potential threats.
WordPress will show a banner if a newer version is available, which you can click to prompt the installation. For plugins and themes, update them via their respective menu in the admin dashboard.
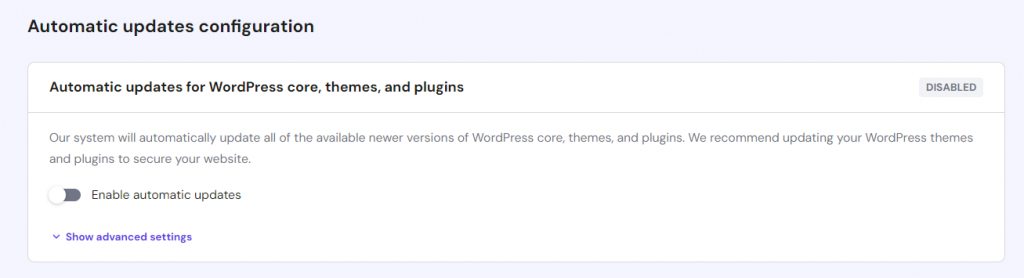
Hostinger users can enable the Auto-update feature on hPanel. Simply navigate to the WordPress menu’s Security section and Enable automatic updates. This feature will automatically patch your core WordPress software, plugins, and themes – ensuring optimal security and performance.
We recommend checking our WordPress monthly round-ups on Hostinger Blog to learn more about the latest news on security vulnerabilities and cyberattacks.
Avoid Using Nulled Plugins and Themes
Nulled plugins and themes are pirated copies of their premium versions. In addition to exposing the website owner to serious legal consequences, using them can present security risks.
The nulled plugin and theme creators usually modify the code to bypass the paywall. Cybercriminals might insert malicious scripts or malware into it, creating an entry point for hacking.
To ensure security and legality, make sure to use official free or premium plugins available in the WordPress repository or third-party stores.
Get a Secure Web Hosting Plan
Your WordPress website is more vulnerable to hacking if your web host doesn’t take server security seriously.
The ideal hosting provider should apply robust security software on their web server. For example, Hostinger infrastructure implements Suhosin PHP hardening, anti-malware protection, and 24/7 monitoring.
Our managed WordPress hosting plan also has additional built-in security tools, like a vulnerability scanner and enhanced DDoS protection. We also offer automatic regular backups to secure your data.

Conclusion
All WordPress websites are susceptible to hacking if not kept secure. If you can’t log in to the wp-admin dashboard or encounter sudden changes on your web page, your site might be under attack.
If you suspect your site has been hacked, immediately put it into maintenance mode to prevent further damage. Reset your password to regain admin dashboard access and remove unknown users from your site.
Then, remove unnecessary extensions and update all software on your website, including the WordPress core. Next, scan for malware, disable PHP execution, and clean your database. These steps will help close entry points for attacks like SQL injection and XSS.
To prevent future hacks, use secure passwords for all accounts and update your software regularly. Install a security plugin and avoid installing pirated software on your website since it might contain malicious code.
Most importantly, make sure your web host has a secure server infrastructure. Hostinger offers a built-in malware scanner, 24/7 infrastructure monitoring, and automatic backups. Our Customer Success team is also available around the clock to help with any issues.
WordPress Hacked FAQ
In this section, we will answer several questions about a hacked WordPress site.
Is WordPress Easily Hacked?
While the WordPress software itself has security measures in place, many hackers target it due to its popularity. Keeping your WordPress up to date is important because more than half of infected WordPress sites run outdated software. If you apply robust security features, follow the best practices, and use a reliable web host, your WordPress site should be safe from hackers.
How to Secure a WordPress Site Without Plugins?
We recommend using a WordPress plugin as it adds additional security layers to your website. If you prefer not to have one, at the minimum, use a strong password on all accounts and limit login attempts by editing the functions.php file. Having a secure hosting plan with built-in security features like a malware scanner also helps.
What Is the Safest CMS?
Drupal is one of the safest CMSs. Its developers optimize the built-in features to maintain optimal performance and test the platform’s security regularly. However, Drupal is more complicated and has a steeper learning curve than WordPress since it is designed for web developers.